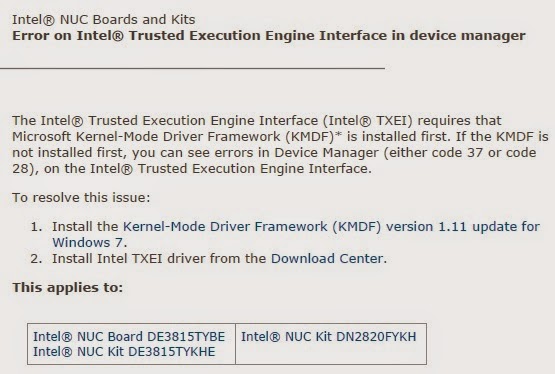
Intel(R) Management Engine Interface driver can be downloaded and installed from your computer's manufacturer's site or Intel's driver download site. Regarding power failure try: Find and fix problems with your computer's power settings to conserve power and extend battery life. If it still continues then get the computer checked by a technician. Descarga los drivers para chipset Intel (R) Atom(TM)/Celeron(R)/Pentium(R) Processor Trusted Execution Engine Interface - 0F18 o instala el software DriverPack. If you have a different computer and/or operating system, try reinstalling the Intel® Trusted Execution Engine Interface (Intel® TXEI) driver: In Device Manager, right-click the device.
- Intel Trusted Execution Engine
- Intel Trusted Execution Engine Interface Driv…
- Intel Trusted Execution Engine Interface Code 10
- Intel Trusted Execution Engine Interface Brix
The terms of the software license agreement included with any software you download will control your use of the software.
EXPRESS BIOS UPDATE
INTEL END USER SOFTWARE LICENSE AGREEMENT
DO NOT DOWNLOAD, INSTALL, ACCESS, COPY, OR USE ANY PORTION OF THE SOFTWARE UNTIL YOU HAVE READ AND ACCEPTED THE TERMS AND CONDITIONS OF THIS AGREEMENT. BY INSTALLING, COPYING, ACCESSING, OR USING THE SOFTWARE, YOU AGREE TO BE LEGALLY BOUND BY THE TERMS AND CONDITIONS OF THIS AGREEMENT. If You do not agree to be bound by, or the entity for whose benefit You act has not authorized You to accept, these terms and conditions, do not install, access, copy, or use the Software and destroy all copies of the Software in Your possession.
This SOFTWARE LICENSE AGREEMENT (this ?Agreement?) is entered into between Intel Corporation, a Delaware corporation (?Intel?) and You. ?You? refers to you or your employer or other entity for whose benefit you act, as applicable. If you are agreeing to the terms and conditions of this Agreement on behalf of a company or other legal entity, you represent and warrant that you have the legal authority to bind that legal entity to the Agreement, in which case, 'You' or 'Your' shall be in reference to such entity. Intel and You are referred to herein individually as a ?Party? or, together, as the ?Parties?.
The Parties, in consideration of the mutual covenants contained in this Agreement, and for other good and valuable consideration, the receipt and sufficiency of which they acknowledge, and intending to be legally bound, agree as follows:
LICENSE. You have a license under Intel?s copyrights to reproduce Intel?s Software only in its unmodified and binary form, (with the accompanying documentation, the ?Software?) for Your personal use only, and not commercial use, in connection with Intel-based products for which the Software has been provided, subject to the following conditions:
- You may not disclose, distribute or transfer any part of the Software, and You agree to prevent unauthorized copying of the Software.
- You may not reverse engineer, decompile, or disassemble the Software.
- You may not sublicense the Software.
- The Software may contain the software and other intellectual property of third party suppliers, some of which may be identified in, and licensed in accordance with, an enclosed license.txt file or other text or file.
- Intel has no obligation to provide any support, technical assistance or updates for the Software.
OWNERSHIP OF SOFTWARE AND COPYRIGHTS. Title to all copies of the Software remains with Intel or its licensors or suppliers. The Software is copyrighted and protected by the laws of the United States and other countries, and international treaty provisions. You may not remove any copyright notices from the Software. Except as otherwise expressly provided above, Intel grants no express or implied right under Intel patents, copyrights, trademarks, or other intellectual property rights. Transfer of the license terminates Your right to use the Software.
DISCLAIMER OF WARRANTY. The Software is provided ?AS IS? without warranty of any kind, EITHER EXPRESS OR IMPLIED, INCLUDING WITHOUT LIMITATION, WARRANTIES OF MERCHANTABILITY OR FITNESS FOR ANY PARTICULAR PURPOSE.
LIMITATION OF LIABILITY. NEITHER INTEL NOR ITS LICENSORS OR SUPPLIERS WILL BE LIABLE FOR ANY LOSS OF PROFITS, LOSS OF USE, INTERRUPTION OF BUSINESS, OR INDIRECT, SPECIAL, INCIDENTAL, OR CONSEQUENTIAL DAMAGES OF ANY KIND WHETHER UNDER THIS AGREEMENT OR OTHERWISE, EVEN IF INTEL HAS BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES.
LICENSE TO USE COMMENTS AND SUGGESTIONS. This Agreement does NOT obligate You to provide Intel with comments or suggestions regarding the Software. However, if You provide Intel with comments or suggestions for the modification, correction, improvement or enhancement of (a) the Software or (b) Intel products or processes that work with the Software, You grant to Intel a non-exclusive, worldwide, perpetual, irrevocable, transferable, royalty-free license, with the right to sublicense, under Your intellectual property rights, to incorporate or otherwise utilize those comments and suggestions.
TERMINATION OF THIS LICENSE. Intel or the sublicensor may terminate this license at any time if You are in breach of any of its terms or conditions. Upon termination, You will immediately destroy or return to Intel all copies of the Software.
U.S. GOVERNMENT RESTRICTED RIGHTS. The Software is a commercial item (as defined in 48 C.F.R. 2.101) consisting of commercial computer software and commercial computer software documentation (as those terms are used in 48 C.F.R. 12.212), consistent with 48 C.F.R. 12.212 and 48 C.F.R 227.72021 through 227.7202-4. You will not provide the Software to the U.S. Government. Contractor or Manufacturer is Intel Corporation, 2200 Mission College Blvd., Santa Clara, CA 95054.
EXPORT LAWS. You agree that neither You nor Your subsidiaries will export/re-export the Software, directly or indirectly, to any country for which the U.S. Department of Commerce or any other agency or department of the U.S. Government or the foreign government from where it is shipping requires an export license, or other governmental approval, without first obtaining any such required license or approval. In the event the Software is exported from the U.S.A. or re-exported from a foreign destination by You, You will ensure that the distribution and export/re-export or import of the Software complies with all laws, regulations, orders, or other restrictions of the U.S. Export Administration Regulations and the appropriate foreign government.
APPLICABLE LAWS. This Agreement and any dispute arising out of or relating to it will be governed by the laws of the U.S.A. and Delaware, without regard to conflict of laws principles. The Parties to this Agreement exclude the application of the United Nations Convention on Contracts for the International Sale of Goods (1980). The state and federal courts sitting in Delaware, U.S.A. will have exclusive jurisdiction over any dispute arising out of or relating to this Agreement. The Parties consent to personal jurisdiction and venue in those courts. A Party that obtains a judgment against the other Party in the courts identified in this section may enforce that judgment in any court that has jurisdiction over the Parties. Your specific rights may vary from country to country.
1. PRIVACY. YOUR PRIVACY RIGHTS ARE SET FORTH IN INTEL?S PRIVACY NOTICE, WHICH FORMS A PART OF THIS AGREEMENT. PLEASE REVIEW THE PRIVACY NOTICE AT HTTPS://WWW.INTEL.COM/PRIVACY TO LEARN HOW INTEL COLLECTS, USES AND SHARES INFORMATION ABOUT YOU.
Intel Trusted Execution Technology (Intel TXT, formerly known as LaGrande Technology) is a computer hardware technology whose primary goals are:
- Attestation of the authenticity of a platform and its operating system.
- Assuring that an authentic operating system starts in a trusted environment, which can then be considered trusted.
- Providing of a trusted operating system with additional security capabilities not available to an unproven one.
Intel TXT uses a Trusted Platform Module (TPM) and cryptographic techniques to provide measurements of software and platform components so that system software as well as local and remote management applications may use those measurements to make trust decisions. It complements Intel Management Engine. This technology is based on an industry initiative by the Trusted Computing Group (TCG) to promote safer computing. It defends against software-based attacks aimed at stealing sensitive information by corrupting system or BIOS code, or modifying the platform's configuration.
- 1Details
Details[edit]
The Trusted Platform Module (TPM) as specified by the TCG provides many security functions including special registers (called Platform Configuration Registers – PCRs) which hold various measurements in a shielded location in a manner that prevents spoofing. Measurements consist of a cryptographic hash using a Secure Hashing Algorithm (SHA); the TPM v1.0 specification uses the SHA-1 hashing algorithm. More recent TPM versions (v2.0+) call for SHA-2.[1][2]
A desired characteristic of a cryptographic hash algorithm is that (for all practical purposes) the hash result (referred to as a hash digest or a hash) of any two modules will produce the same hash value only if the modules are identical.
Measurements[edit]
Measurements can be of code, data structures, configuration, information, or anything that can be loaded into memory. TCG requires that code not be executed until after it has been measured. To ensure a particular sequence of measurements, hash measurements in a sequence are not written to different PCRs, but rather a PCR is 'extended' with a measurement. This means that the TPM takes the current value of the PCR and the measurement to be extended, hashes them together, and replaces the content of the PCR with that hash result. The effect is that the only way to arrive at a particular measurement in a PCR is to extend exactly the same measurements in exactly the same order. Therefore, if any module being measured has been modified, the resulting PCR measurement will be different and thus it is easy to detect if any code, configuration, data, etc. that has been measured had been altered or corrupted. The PCR extension mechanism is crucial to establishing a Chain of trust in layers of software (see below).
Chain of trust[edit]
The technology supports both a static chain of trust and a dynamic chain of trust. The static chain of trust starts when the platform powers on (or the platform is reset), which resets all PCRs to their default value. For server platforms, the first measurement is made by hardware (i.e., the processor) to measure a digitally signed module (called an Authenticated Code Module or ACM) provided by the chipset manufacturer. The processor validates the signature and integrity of the signed module before executing it. The ACM then measures the first BIOS code module, which can make additional measurements.
The measurements of the ACM and BIOS code modules are extended to PCR0, which is said to hold the static core root of trust measurement (CRTM) as well as the measurement of the BIOS Trusted Computing Base (TCB). The BIOS measures additional components into PCRs as follows:
- PCR0 – CRTM, BIOS code, and Host Platform Extensions[a]
- PCR1 – Host Platform Configuration
- PCR2 – Option ROM Code
- PCR3 – Option ROM Configuration and Data
- PCR4 – IPL (Initial Program Loader) Code (usually the Master Boot Record – MBR)
- PCR5 – IPL Code Configuration and Data (for use by the IPL Code)
- PCR6 – State Transition and Wake Events
- PCR7 – Host Platform Manufacturer Control

The dynamic chain of trust starts when the operating system invokes a special security instruction, which resets dynamic PCRs (PCR17–22) to their default value and starts the measured launch. The first dynamic measurement is made by hardware (i.e., the processor) to measure another digitally signed module (referred to as the SINIT ACM) which is also provided by the chipset manufacturer and whose signature and integrity are verified by the processor. This is known as the Dynamic Root of Trust Measurement (DRTM).
The SINIT ACM then measures the first operating system code module (referred to as the measured launch environment – MLE). Before the MLE is allowed to execute, the SINIT ACM verifies that the platform meets the requirements of the Launch Control Policy (LCP) set by the platform owner. LCP consists of three parts:
- Verifying that the SINIT version is equal or newer than the value specified
- Verifying that the platform configuration (PCONF) is valid by comparing PCR0–7 to known-good values (the platform owner decides which PCRs to include)
- Verifying that the MLE is valid, by comparing its measurement to a list of known-good measurements.
The integrity of the LCP and its lists of known-good measurements are protected by storing a hash measurement of the policy in the TPM in a protected non-volatile location that can only be modified by the platform owner.
Execute as a Trusted OS[edit]
Once the LCP is satisfied, the SINIT ACM allows the MLE to execute as a Trusted OS by enabling access to special security registers and enabling TPM Locality 2 level access. The MLE is now able to make additional measurements to the dynamic PCRs. The dynamic PCRs contain measurement of:
- PCR17 – DRTM and launch control policy
- PCR18 – Trusted OS start-up code (MLE)
- PCR19 – Trusted OS (for example OS configuration)
- PCR20 – Trusted OS (for example OS Kernel and other code)
- PCR21 – as defined by the Trusted OS
- PCR22 – as defined by the Trusted OS
The technology also provides a more secure way for the operating system to initialize the platform. In contrast to the normal processor initialization [which involved the boot-strap-processor (BSP) sending a Start-up Inter-Processor Interrupt (SIPI) to each Application Processor, thus starting each processor in 'real mode' and then transitioning to 'virtual mode' and finally to 'protected mode'], the operating system avoids that vulnerability by performing a secure launch (a.k.a. measured launch) which puts the Application Processors in a special sleep state from which they are directly started in protected mode with paging on, and are not allowed to leave this state.[3]
Application[edit]
PCR values are available both locally and remotely. Furthermore, the TPM has the capability to digitally sign the PCR values (i.e., a PCR Quote) so that any entity can verify that the measurements come from, and are protected by, a TPM, thus enabling Remote Attestation to detect tampering, corruption, and malicious software. Additionally, those values can be used to identify the execution environment (the particular BIOS version, OS level, configuration, etc.) and compare them to their own lists of known-good values to further categorize the platform. This ability to evaluate and assign trust levels to platforms is known as Trusted Compute Pools.
Some examples of how Trusted Compute Pools are used:
- Isolation – the ability to control if a platform connects to the production network or is quarantined based on its trust level or failure to pass its launch control policy.
- Trust Based Policy – such as restricting critical apps to only execute on platforms that meet a specified trust level
- Compliance and Auditing – demonstrating that critical, personal, or sensitive data has only been processed on platforms that meet trust requirements
Numerous server platforms include Intel TXT, and TXT functionality is leveraged by software vendors including HyTrust, PrivateCore, Citrix, and VMware. Open-source projects also utilize the TXT functionality; for example, tboot provides a TXT-based integrity system for the Linux kernel and Xen hypervisor.[4][5]
Intel Trusted Execution Engine
See also[edit]
Intel Trusted Execution Engine Interface Driv…
Notes[edit]
- ^CRTM is measured by the processor and initial BIOS code is measured by the ACM (all other measurements made by BIOS or other firmware code) but only after that code had been measured.
References[edit]
Intel Trusted Execution Engine Interface Code 10
- ^'SHA-1 Uses in TPM v1.2'. Trusted Computing Group. Retrieved 2014-03-14.
- ^'TPM 2.0 Library Specification FAQ'. Trusted Computing Group. Retrieved 2014-03-14.
- ^'Chapter 2.2: MLE Launch'. Intel Trusted Execution Technology (Intel® TXT) Software Development Guide(PDF). Intel.
- ^'tboot (Trusted Boot)'. sourceforge.net. October 6, 2014. Retrieved November 16, 2014.
- ^Joseph Cihula (February 28, 2011). 'Trusted Boot: Verifying the Xen Launch'(PDF). xenproject.org. Retrieved November 16, 2014.
Intel Trusted Execution Engine Interface Brix
External links[edit]
- 'Trusted Execution', Technology, Intel.
- 'Trusted Execution', Technology(PDF) (overview), Intel.
- 'Trusted Execution', Technology(PDF) (architectural overview), Intel.
- Intel Trusted Execution Technology Software Development Guide(PDF), Intel.
- 'Virtualization', Technology, Intel.
- Intel TXT Overview, part of Linux kernel documentation, December 1, 2014
- Integrity management using Intel TXT, LWN.net, April 1, 2009, by Jake Edge
- Attacking Intel Trusted Execution Technology, Black Hat Briefings, February 2009, by Rafal Wojtczuk and Joanna Rutkowska
- Trusted Computing Technologies, Intel Trusted Execution Technology, Sandia National Laboratories, January 2011, by Jeremy Daniel Wendt and Max Joseph Guise